Sponsored by Exabeam
Sponsored by VMware
Blueprint for a Future Ready Workforce: A 3-Stage Approach
Sponsored by Menlo Security
Securing the Future of Work
Sponsored by Barracuda
The Evolution of Email Security
Sponsored by CyberGRX
Third-Party Cyber Risks in the Financial Industry
Sponsored by CyberGRX
Third-Party Cyber Risks in the Oil & Gas Industry
Sponsored by CyberGRX
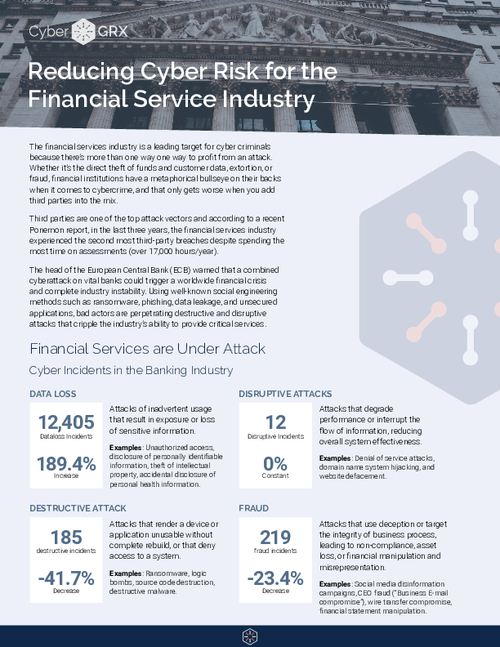
Reducing Cyber Risk for the Financial Service Industry
Sponsored by CyberGRX
CyberGRX Exchange Insights
Sponsored by Ordr
EMA Zero Trust Networking Research Summary
Sponsored by Ordr
5 Ways to Improve Asset Inventory and Management Using Ordr
Sponsored by Gigamon
TLS Versions: North-South and East-West Web Traffic Analysis
Sponsored by Omada
Forrester Best Practices: Identity Management And Governance
Sponsored by Omada
Gartner Market Guide
Sponsored by Hitachi ID Systems
How to Move Faster Against Cyber Automated Attacks
Sponsored by Verve Industrial