Endpoint Security , Governance & Risk Management , Internet of Things Security
New Online Platform Coordinates IoT Bug Reports
VulnerableThings.com Seeks to Improve Bug Reporting for Connected Devices
Can the reporting and delivery of information about software flaws in IoT devices be improved?
See Also: Improving OT and IoT Security for Substations and Power Grids
Almost certainly. A big issue with fixing vulnerabilities in IoT devices is getting the attention of manufacturers and then distributing advice to organizations running vulnerable devices.
The IoT Security Foundation, based in the U.K., and Oxford Information Labs, an Oxford University-based consultancy, are hoping to close the gap with an online platform called VulnerableThings.com. The platform will collate bug reports, distribute them to vendors and open a communication channel between researchers and companies.
“It is our intention to provide a low-cost tool to help IoT vendors manage vulnerability reports, simplify communication with IoT researchers and provide access to useful materials and consultants who can help,” according to a statement from the new organization.
The platform is designed to help vendors comply with new IoT regulations and standards, which have been enacted or are under consideration in many regions, including the U.S., the U.K., Australia and the European Union (see: Federal IoT Guidelines Move Closer to Becoming Law).
Free Pilot Program
Vulnerable Things has been seed-funded by the U.K. government, which has been working to improve IoT security by developing a code of practice for consumer IoT manufacturers.
The U.K. also has developed legislation for a labeling program that spells out how an IoT device will be supported and legislation requiring that IoT products meet basic security requirements.
The U.S. and U.K. will likely require vulnerability disclosure programs for IoT makers, says Brad Ree, CTO of the consultancy ioXt and board member at the ioXt Alliance, a trade group dedicated to securing IoT devices. ioXt runs a certification program where manufacturers can submit devices for testing to ensure they meet appropriate security levels, and it requires companies to have a vulnerability disclosure program.
“Not all companies have the experience to run their own vulnerability disclosure program, which is why organizations such as ioXt and VulnerableThings can help their membership,” Ree says.
Vulnerable Things, which is in pilot testing, will be free to use until Jan. 31. Organizers say a small annual fee may be required after testing ends.
Manufacturers that subscribe will have a dashboard that connects them with the individual who found a vulnerability and helps with the resolution process. For manufacturers that haven’t registered with Vulnerable Things, an alert will be sent to a public email address of the manufacturer. The company will be granted secure access to the details of the flaw.
The platform will accept reports from anonymous researchers. But those who are registered will get access to their own dashboard to see the progress of issues they’ve raised with various companies.
IoT Vulnerable Disclosure Failures
Governments and enterprises have become more concerned over the last few years about how IoT can pose security risks to consumers as well as on the national security level. Some experts say IoT manufacturers push products to market too soon without conducting thorough code reviews, set default authentication credentials and leave open ports (see: Want Your Coffee Machine Back? Pay a Ransom).
Security researchers often complain that IoT manufacturers may not respond to vulnerability reports or never actually fix the devices. One big drive in the U.K., U.S. and elsewhere is to get IoT manufacturers to commit to providing a set support period in which software updates and patches will be delivered.
Two years ago, the IoT Security Foundation conducted research to assess the state of vulnerability disclosure practices in consumer IoT companies. It found that less than 10% of 330 companies had vulnerability disclosure policies.
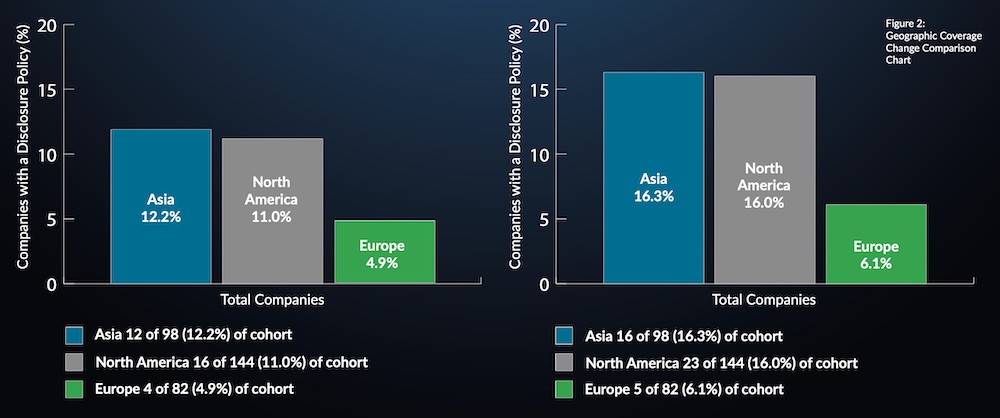
The foundation repeated the study one year later and released the results earlier this month. Almost half of the companies studied were in North America with the remainder in Asia and Europe. The study found some meager improvement. In 2018, only 9.7% of companies, or 32, had vulnerability disclosure policies. That number went up to 13.3%, or 44 companies, in 2019.
“The sooner a researcher can identify the correct point of contact for communicating their findings to a firm, the faster the company can begin the process to address the security issues,” the latest study says. “This in turn reduces the potential exploitation and risk of that vulnerability.”
The percentage of Asian companies with vulnerability disclosure policies - 16. 3% - was slightly higher than those in North America, at 16%. Europe lagged at 6.1%.
“The European cohort compares very poorly against both Asia and North America yet all have significant room for improvement,” the foundation says in its report. “Or to put it another way, Asia is the best of a bad lot.”
The study also looked at whether manufacturers were using “security.txt,” which allows organizations to make it easy for security researchers to find the right security contact to whom to report issues. It involves simply creating a security.txt file in the .well-known directory.
But that step hasn’t caught on. Just 0.9% percent of manufacturers were using security.txt. And only 4.2% had a /security page on their site – such as www.apple.com/security – or used one to redirect people to their actual security pages, the foundation says.



















