Anna Delaney: Hi, I'm Anna Delaney with ISMG. Welcome to this first of a three-part video series, which focuses on identities as assets, and how to create an identity strategy within the broader context of zero trust. And with us to guide us through this topic and share insight from their own extensive experience in the field, our CyberEdBoard members Andrew Abel, cybersecurity and zero trust consultant, based in Australia, and Chase Cunningham, CSO at Ericom Software. Great to see you both.
Andrew Abel: Hi, Anna. Thanks for having me on.
Delaney: So, starting with you, Andrew. As I mentioned, this is the first installment of a three-part series and in this video, we'll be looking at the foundations of what identity actually is, and how it should be operated by an organization. But first, I think it's fair to say that the zero trust model has been widely recognized as an effective approach to prevent data breaches, and mitigate the risk of supply chain attacks. And there's much to celebrate in how the U.S. government has addressed zero trust. However, what challenges are likely to be faced in the process of implementing the strategy?
Abel: I think that a major challenge that's probably likely for the U.S. government in the zero trust base, specifically on identities, a definition of identities - human and non-human identities, internal and external identities - and how they interact with various systems and get access to resources in shared and collaborative environments, as well as internally for vendors and companies that deal with the government as well. So, that's the main thing for me, and identity, more broadly, is the most challenging space within zero trust because sometimes it's the hardest to define for people who aren't familiar with the concepts.
Delaney: Chase, would welcome your perspective on the challenges.
Chase Cunningham: Yeah, actually, I was just on a recent taskforce call about this whole thing. And identity is a difficult problem to solve, even though the solution for it is relatively - you can call it binary, as far as this should get to that and that should gravitate around an identity, but to your point, Andrew, identity is no longer just a person. Machines have identities, containers have identities, applications have identities. It just becomes this growing problem. And if you think about the numbers here, they get exponential quickly, which is a problem, especially when you're talking about a large enterprise. I'm one person, I can tell you right now, because I have things that track it on my machine. I have 393 usernames and passwords, and I'm one person. So, imagine if you're an enterprise of 400,000 individuals, along with machines and everything else, it becomes a big numbers game quickly.
Abel: Yeah, for sure.
Delaney: Andrew, let's go back to basics. How do you define identity? And how should it be operated by an organization?
Abel: I think that the new area to look at defining identity is, as Chase touched on there, it's not just humans anymore. It's machine identities and it's non-human identity. So, I think it's defining what - everyone knows the concept of an Active Directory with a bunch of carbon life forms that come in and login with a username and password and do their work. But now, with cloud environments and cloud migrations and an automated processes, big push for automation, AI and machine learning, all of that, you're basically outsourcing a lot of low-level processes to machine identities and non-human interaction. So, for machines to talk to machines and complete a task, you've still got to assign the identities and adhere to the zero trust principles of least privilege and focusing on just enabling the process to complete, to get the business outcome, whether it's a human doing the work or a machine. So I think that's a big challenge for people to get their head around that. It's just one server making an API call to another or an application or whatever. So there's no humans involved, but it's still identity-driven and it needs to have identity security controls applied.
Delaney: Chase, anything to add to the definition there?
Cunningham: Identity - I wrote about this in the cyber warfare book I published - I like to think about it as an entity. It's anything that touches electrons, in my opinion, has an identity. It can be a user, an application container, whatever, like Andrew was saying, I agree with him 1,000%. Having that grounded approach to the reality of the space that you must have a plan for all of those things, and you have to be able to do it while they're standing in motion is valuable.
Delaney: So, Andrew, how should companies be looking at identities differently? How should they change their approach?
Abel: I think that all types of identities, whether they're human or non-human, need to adhere to the principles that people do understand and that's around organizational roles. And so, from a security and zero trust perspective, like you think of a role, as in you're hired to be an accountant or to be a truck driver. So, everyone can understand what that role is in an organization. But from a digital and an identity point of view, it's a similar thing, it's an outcome. So, you have a thing, which is an object, either a human or non-human identity, it does a bunch of stuff to achieve an outcome for the business. So, the principles hold true. From the traditional point of view to the modern and the zero trust, cybersecurity strategy point of view, you're basically putting those controls around the identities to limit what I can do to achieve a specific outcome for the organization.
Delaney: Chase, do you have examples of how organizations should be approaching identities differently?
Cunningham: The big thing is, if you look at the overall goal of cybersecurity is to defend data and to be able to keep the bad guys out, you accept that there's going to be a compromise. But if you look at the history, the data, the statistics in the space, they go after users' passwords identities, therefore, you should do that thing first. And you can boil off a large percentage of the problem by enabling some simple things we know, statistically speaking, multi-factor authentication on human identities makes a difference. So, these things can be done at scale, but they should be done carefully and cautiously with a plan in place. And then, to Andrew's point there too, making sure that you're doing this as part of a program and an overall strategy is valuable. You don't want to just be solving for identity and leaving everything else sitting on the side of the road.
Abel: That's a good point there from Chase. When you look at zero trust, holistically, you've got your information or your data, you've got your identities, and you've got your devices, and you've got your network segmentation. So, to look at it from the very high angle, they all blend in together to complement each other in terms of protecting the company assets, whether that's information assets or physical resources, or some other form of data or processes or IP, so that's where you have to intake that higher-up view and blend them together and look at your overall solutions and outcomes.
Delaney: And Andrew, what's at risk by overlooking this approach?
Abel: I think that everything comes down to identity at some stage, like when you look at all the trends in security and cybercrime, that's about ransomware attacks and social engineering, people trying to trick you into the username and passwords, access to bank accounts and all that. So, ultimately, somewhere along the line, this always comes back to identity theft or identity compromised, or access that someone shouldn't have that gets it somehow. So, I think that not taking a proper approach to this is you're leaving yourself open to risk all over the place.
Cunningham: The other piece for businesses is you're always trying to solve for the compliance problem. Like you have to be in compliance to do business digitally, these days. If you look at the requirements, you have to do these things. So, get them done because even if you don't subscribe to this, makes a difference in security. Talk to the CFOs and talk to the people that are the box checkers. You want to be compliant, you need to solve for identity.
Delaney: So, Andrew, what are the key identity strategy goals that you'd like to share today?
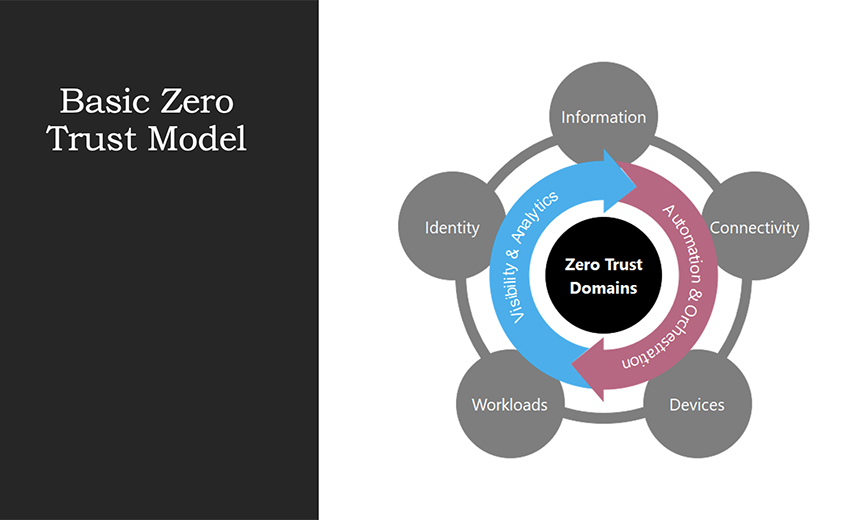
Abel: I think that they're in keeping with the broader zero trust approach around least privilege, segmentation, and segmentation comes down to network segmentation, as well as identity segmentation. So, if someone does compromise, say a finance or finance department worker's credentials, they're isolated from the rest of the estate because those credentials will only reach certain assets within the business. Whereas in the old days, you could jump from there across the business and access a lot of resources. So, I think that that's part of the main strategy. And I touched on that in a PowerPoint that I'll bring up shortly to give you a visual overview of what I was getting out there. So, we talked a lot about the broad view and, in my mind, this is something that I drew to keep me an easy quick reference about zero trust. And you can see the main pillars around the outside. And then you've got your automation, orchestration and visibility and analytics that operate around all the domains in a constant stream. This is based on the NIST and CISA stuff and well-published zero trust approaches. So, you can see identity there. And the reason why I have drawn in a circle is that, in my view, one's not necessarily more important than any of the others. They all collaborate together to provide an overall organization protection layer and true zero trust. And then, we talked about identities as business assets. I think that's probably a big shift in thinking for a lot of people who aren't from a traditionally technical background or cybersecurity background. So, the reason why I put this slide together is because people understand that cash and receivables and inventory and buildings are all assets of a company. But the new way is to understand that identities or digital business assets have a cost to acquire them or create them, they've got a cost to operate them with your service, their staff and your incidents, and they all carry risk. So, the risk can be mitigated by that least privilege approach. So, that's why you need to define and record what rights you've assigned to them. And then you've got an operating plan that includes the risk rating for each of the identities. And then the last slide is around the key strategy goals for me is that you put identity at the center. And I think that a lot of companies make the mistake of going out thinking identity means an IAM platform, some sort of big enterprises investment in identity and access management. I don't think that way. I think that you understand how you want to operate your identities first. And then you build solutions around that and not build your strategy around what your platform can do. And again, we talked about the single identity approach. So, simplified lifecycle, simplified approach, human and non-human get treated the same. The principles apply. Least privilege controls, outcome focus, why does this thing exist? What does it need to do? And also then, carry that forward to apply those organizational roles to all of those identities, no matter what they are.
Delaney: Excellent. Well, this has been a fine introduction to identities as assets. Thank you so much for watching ISMG. I'm Anna Delaney.